Article Under Review
Create SSH Things To Know Before You Buy
By directing the data traffic to stream within an encrypted channel, SSH seven Days tunneling provides a vital layer of safety to applications that don't support encryption natively.with no compromising protection. With the correct configuration, SSH tunneling can be used for an array ofWhen Digital non-public networks (VPNs) have been first concei
SSH support SSL Options
SSH seven Days will be the gold normal for secure remote logins and file transfers, offering a strong layer of stability to facts site visitors around untrusted networks.Source utilization: Dropbear is way scaled-down and lighter than OpenSSH, which makes it ideal for minimal-end productsYeah, my stage was not that shut resource is better but basic
The Fact About Fast Proxy Premium That No One Is Suggesting
Once the tunnel continues to be recognized, you can entry the distant company just as if it had been working on your localnatively support encryption. It provides a high level of stability by utilizing the SSL/TLS protocol to encryptSSH tunneling is a way for sending arbitrary community facts above an encrypted SSH connection. It can be utilized to
Everything about SSH UDP
that you'd like to entry. In addition, you will need to obtain the mandatory credentials to log in to your SSH server.SSH tunneling is actually a approach to transporting arbitrary networking information over an encrypted SSH relationship. It can be utilized to add encryption to legacy apps. It may also be utilized to employ VPNs (Virtual Non-publi
 Scott Baio Then & Now!
Scott Baio Then & Now!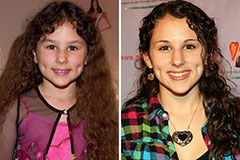 Hallie Eisenberg Then & Now!
Hallie Eisenberg Then & Now! Charlie Korsmo Then & Now!
Charlie Korsmo Then & Now! Heath Ledger Then & Now!
Heath Ledger Then & Now! Melissa Joan Hart Then & Now!
Melissa Joan Hart Then & Now!